Automaticaly update Route 53 DNS record from EC2
Introduction
Learn to update a Route 53-managed DNS record automatically from an EC2 instance, even with a dynamic IP address. Helps with 5 Elastic IP default limit.
Ensures website remains accessible despite IP changes. Simple implementation and guarantees a seamless experience without DNS issues.
How it will work?
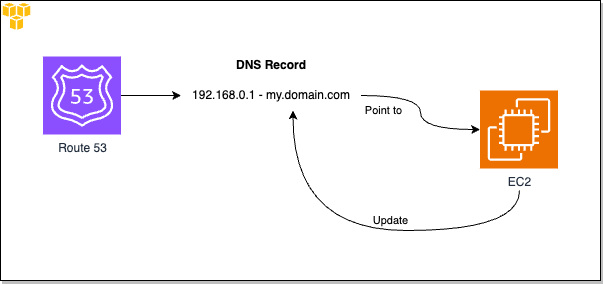
When an EC2 instance is launched, a dynamic IP address is assigned to it. Subsequently, it is feasible to update the necessary DNS record within Route 53 by utilizing effective scripting methods based on EC2 tags. This article will guide you through the process of implementing such a method.
Prerequisites
Before going straight to automate this process, some prerequisites must be checked. You must:
- be able to create custom IAM policies within AWS
- have access to Route 53 with create rights
- you must have a root access to the EC2 instance
Time to act!
Route 53
Firstly, you need to create a dedicated “A” record.
As first target IP, you can set-up a random IP (e.g. 1.1.1.1 in this example).
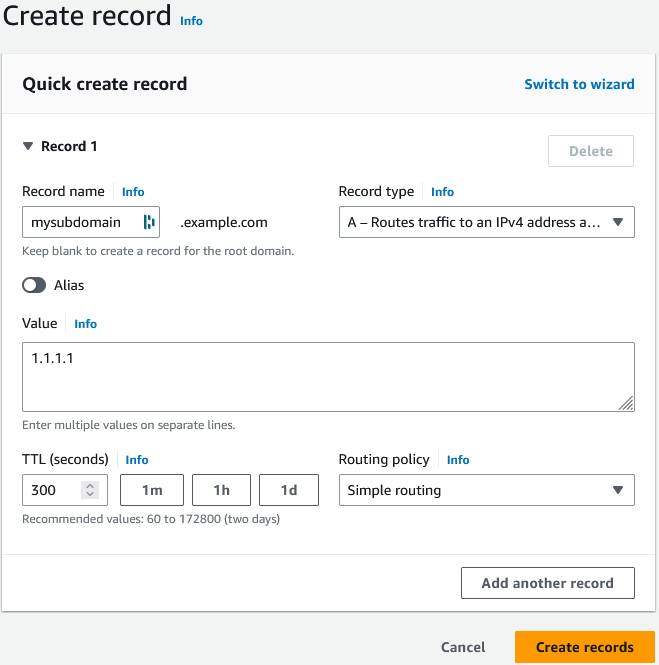
Consider setting a low TTL to minimize service disruption. Shorter cache duration results in a more efficient and reliable service experience.
IAM
First, we will create a dedicated policy to allow:
- Route 53 update
- Retrieve instance information
Navigate to IAM > Policies, and launch the Create Policy wizzard. Use below code as JSON source.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "ListTags",
"Effect": "Allow",
"Action": "ec2:DescribeTags",
"Resource": "*"
},
{
"Sid": "UpdateDNS",
"Effect": "Allow",
"Action": "route53:ChangeResourceRecordSets",
"Resource": "arn:aws:route53:::hostedzone/*"
}
]
}Click Next and name the policy as you prefer, then click Create Policy.
Last IAM step is to create a dedicated role for your EC2 with attached policy.
Navigate to IAM > Roles and launch the Create Role wizzard.
As Trusted entity type, choose AWS Service and EC2 as Use case. Click Next.
In the list of policies, search and select previously created policy.
Click on Next, name the IAM role and Create role.
EC2
AWS Console
Through the AWS Console, navigate to EC2 instance list and select your instance.
Click on Actions > Security > Modify IAM role.
In the dropdown list, select the role we create at previous step and click Update IAM role.
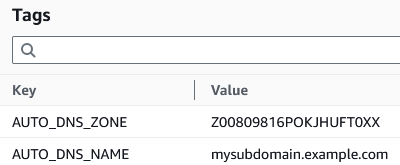
Finally, we will add 2 tags to your instance as shown in the example below:
- DNS Zone:
- Name: AUTO_DNS_ZONE
- Value: <<Your DNS Zone ID>>
- Domain Name:
- Name: AUTO_DNS_NAME
- Value: <<FQDN of the record you want to update>>
On server
Connect and log in to your server. Create a script file as below:
#!/bin/bash
# Get token
TOKEN=$(curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600")
# Retrieve instance information (ID, Zone, public IP)
INSTANCE_ID=$(curl -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/instance-id/)
AZ=$(curl -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/placement/availability-zone/)
MY_IP=$(curl -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/public-ipv4/)
# Extract tags associated with instance
ZONE_TAG=$(aws ec2 describe-tags --region ${AZ::-1} --filters "Name=resource-id,Values=${INSTANCE_ID}" --query 'Tags[?Key==`AUTO_DNS_ZONE`].Value' --output text)
NAME_TAG=$(aws ec2 describe-tags --region ${AZ::-1} --filters "Name=resource-id,Values=${INSTANCE_ID}" --query 'Tags[?Key==`AUTO_DNS_NAME`].Value' --output text)
# Update Route 53 Record Set based on retrieved information
aws route53 change-resource-record-sets --hosted-zone-id $ZONE_TAG --change-batch '{"Changes":[{"Action":"UPSERT","ResourceRecordSet":{"Name":"'$NAME_TAG'","Type":"A","TTL":300,"ResourceRecords":[{"Value":"'$MY_IP'"}]}}]}'Save and place this script into the following folder:
/var/lib/cloud/scripts/per-boot
This script will be executed everytime the server starts.
Test it!
In order to test it properly, you must fully Stop & Start your instance. A reboot doesn’t renew the IP everytime.

